A Guide to Convolutional Neural Networks for Computer Vision
Computer vision has become increasingly important and effective in recent years due to its wide-ranging applications in areas as diverse as smart surveillance and monitoring, health and medicine, sports and recreation, robotics, drones, and self-driving cars. Visual recognition tasks, such as image classification, localization, and detection, are the core building blocks of many of these applications, and recent developments in Convolutional Neural Networks (CNNs) have led to outstanding performance in these state-of-the-art visual recognition tasks and systems. As a result, CNNs now form the crux of deep learning algorithms in computer vision. This self-contained guide will benefit those who seek to both understand the theory behind CNNs and to gain hands-on experience on the application of CNNs in computer vision. It provides a comprehensive introduction to CNNs starting with the essential concepts behind neural networks: training, regularization, and optimization of CNNs.The book also discusses a wide range of loss functions, network layers, and popular CNN architectures, reviews the different techniques for the evaluation of CNNs, and presents some popular CNN tools and libraries that are commonly used in computer vision. Further, this text describes and discusses case studies that are related to the application of CNN in computer vision, including image classification, object detection, semantic segmentation, scene understanding, and image generation. This book is ideal for undergraduate and graduate students, as no prior background knowledge in the field is required to follow the material, as well as new researchers, developers, engineers, and practitioners who are interested in gaining a quick understanding of CNN models.
Metric Learning
Similarity between objects plays an important role in both human cognitive processes and artificial systems for recognition and categorization. How to appropriately measure such similarities for a given task is crucial to the performance of many machine learning, pattern recognition and data mining methods. This book is devoted to metric learning, a set of techniques to automatically learn similarity and distance functions from data that has attracted a lot of interest in machine learning and related fields in the past ten years. In this book, we provide a thorough review of the metric learning literature that covers algorithms, theory and applications for both numerical and structured data. We first introduce relevant definitions and classic metric functions, as well as examples of their use in machine learning and data mining. We then review a wide range of metric learning algorithms, starting with the simple setting of linear distance and similarity learning. We show how one may scale-up these methods to very large amounts of training data. To go beyond the linear case, we discuss methods that learn nonlinear metrics or multiple linear metrics throughout the feature space, and review methods for more complex settings such as multi-task and semi-supervised learning. Although most of the existing work has focused on numerical data, we cover the literature on metric learning for structured data like strings, trees, graphs and time series. In the more technical part of the book, we present some recent statistical frameworks for analyzing the generalization performance in metric learning and derive results for some of the algorithms presented earlier. Finally, we illustrate the relevance of metric learning in real-world problems through a series of successful applications to computer vision, bioinformatics and information retrieval. Table of Contents: Introduction / Metrics / Properties of Metric Learning Algorithms / Linear Metric Learning / Nonlinear and Local Metric Learning / Metric Learning for Special Settings / Metric Learning for Structured Data / Generalization Guarantees for Metric Learning / Applications / Conclusion / Bibliography / Authors' Biographies
Judgment Aggregation
Judgment aggregation is a mathematical theory of collective decision-making. It concerns the methods whereby individual opinions about logically interconnected issues of interest can, or cannot, be aggregated into one collective stance. Aggregation problems have traditionally been of interest for disciplines like economics and the political sciences, as well as philosophy, where judgment aggregation itself originates from, but have recently captured the attention of disciplines like computer science, artificial intelligence and multi-agent systems. Judgment aggregation has emerged in the last decade as a unifying paradigm for the formalization and understanding of aggregation problems. Still, no comprehensive presentation of the theory is available to date. This Synthesis Lecture aims at filling this gap presenting the key motivations, results, abstractions and techniques underpinning it. Table of Contents: Preface / Acknowledgments / Logic Meets Social Choice Theory / Basic Concepts /Impossibility / Coping with Impossibility / Manipulability / Aggregation Rules / Deliberation / Bibliography / Authors' Biographies / Index
Representing and Reasoning with Qualitative Preferences
This book provides a tutorial introduction to modern techniques for representing and reasoning about qualitative preferences with respect to a set of alternatives. The syntax and semantics of several languages for representing preference languages, including CP-nets, TCP-nets, CI-nets, and CP-theories, are reviewed. Some key problems in reasoning about preferences are introduced, including determining whether one alternative is preferred to another, or whether they are equivalent, with respect to a given set of preferences. These tasks can be reduced to model checking in temporal logic. Specifically, an induced preference graph that represents a given set of preferences can be efficiently encoded using a Kripke Structure for Computational Tree Logic (CTL). One can translate preference queries with respect to a set of preferences into an equivalent set of formulae in CTL, such that the CTL formula is satisfied whenever the preference query holds. This allows us to use a model checker toreason about preferences, i.e., answer preference queries, and to obtain a justification as to why a preference query is satisfied (or not) with respect to a set of preferences. This book defines the notions of the equivalence of two sets of preferences, including what it means for one set of preferences to subsume another, and shows how to answer preferential equivalence and subsumption queries using model checking. Furthermore, this book demontrates how to generate alternatives ordered by preference, along with providing ways to deal with inconsistent preference specifications. A description of CRISNER--an open source software implementation of the model checking approach to qualitative preference reasoning in CP-nets, TCP-nets, and CP-theories is included, as well as examples illustrating its use.
Game Theory for Data Science
Intelligent systems often depend on data provided by information agents, for example, sensor data or crowdsourced human computation. Providing accurate and relevant data requires costly effort that agents may not always be willing to provide. Thus, it becomes important not only to verify the correctness of data, but also to provide incentives so that agents that provide high-quality data are rewarded while those that do not are discouraged by low rewards. We cover different settings and the assumptions they admit, including sensing, human computation, peer grading, reviews, and predictions. We survey different incentive mechanisms, including proper scoring rules, prediction markets and peer prediction, Bayesian Truth Serum, Peer Truth Serum, Correlated Agreement, and the settings where each of them would be suitable. As an alternative, we also consider reputation mechanisms. We complement the game-theoretic analysis with practical examples of applications in prediction platforms, community sensing, and peer grading.
An Introduction to the Planning Domain Definition Language
Planning is the branch of Artificial Intelligence (AI) that seeks to automate reasoning about plans, most importantly the reasoning that goes into formulating a plan to achieve a given goal in a given situation. AI planning is model-based: a planning system takes as input a description (or model) of the initial situation, the actions available to change it, and the goal condition to output a plan composed of those actions that will accomplish the goal when executed from the initial situation. The Planning Domain Definition Language (PDDL) is a formal knowledge representation language designed to express planning models. Developed by the planning research community as a means of facilitating systems comparison, it has become a de-facto standard input language of many planning systems, although it is not the only modelling language for planning. Several variants of PDDL have emerged that capture planning problems of different natures and complexities, with a focus on deterministic problems. The purpose of this book is two-fold. First, we present a unified and current account of PDDL, covering the subsets of PDDL that express discrete, numeric, temporal, and hybrid planning. Second, we want to introduce readers to the art of modelling planning problems in this language, through educational examples that demonstrate how PDDL is used to model realistic planning problems. The book is intended for advanced students and researchers in AI who want to dive into the mechanics of AI planning, as well as those who want to be able to use AI planning systems without an in-depth explanation of the algorithms and implementation techniques they use.
The Four Generations of Entity Resolution
Entity Resolution (ER) lies at the core of data integration and cleaning and, thus, a bulk of the research examines ways for improving its effectiveness and time efficiency. The initial ER methods primarily target Veracity in the context of structured (relational) data that are described by a schema of well-known quality and meaning. To achieve high effectiveness, they leverage schema, expert, and/or external knowledge. Part of these methods are extended to address Volume, processing large datasets through multi-core or massive parallelization approaches, such as the MapReduce paradigm. However, these early schema-based approaches are inapplicable to Web Data, which abound in voluminous, noisy, semi-structured, and highly heterogeneous information. To address the additional challenge of Variety, recent works on ER adopt a novel, loosely schema-aware functionality that emphasizes scalability and robustness to noise. Another line of present research focuses on the additional challenge ofVelocity, aiming to process data collections of a continuously increasing volume. The latest works, though, take advantage of the significant breakthroughs in Deep Learning and Crowdsourcing, incorporating external knowledge to enhance the existing words to a significant extent. This synthesis lecture organizes ER methods into four generations based on the challenges posed by these four Vs. For each generation, we outline the corresponding ER workflow, discuss the state-of-the-art methods per workflow step, and present current research directions. The discussion of these methods takes into account a historical perspective, explaining the evolution of the methods over time along with their similarities and differences. The lecture also discusses the available ER tools and benchmark datasets that allow expert as well as novice users to make use of the available solutions.
General Game Playing
General game players are computer systems able to play strategy games based solely on formal game descriptions supplied at "runtime" (n other words, they don't know the rules until the game starts). Unlike specialized game players, such as Deep Blue, general game players cannot rely on algorithms designed in advance for specific games; they must discover such algorithms themselves. General game playing expertise depends on intelligence on the part of the game player and not just intelligence of the programmer of the game player. GGP is an interesting application in its own right. It is intellectually engaging and more than a little fun. But it is much more than that. It provides a theoretical framework for modeling discrete dynamic systems and defining rationality in a way that takes into account problem representation and complexities like incompleteness of information and resource bounds. It has practical applications in areas where these features are important, e.g., in business andlaw. More fundamentally, it raises questions about the nature of intelligence and serves as a laboratory in which to evaluate competing approaches to artificial intelligence. This book is an elementary introduction to General Game Playing (GGP). (1) It presents the theory of General Game Playing and leading GGP technologies. (2) It shows how to create GGP programs capable of competing against other programs and humans. (3) It offers a glimpse of some of the real-world applications of General Game Playing.
Federated Learning
How is it possible to allow multiple data owners to collaboratively train and use a shared prediction model while keeping all the local training data private? Traditional machine learning approaches need to combine all data at one location, typically a data center, which may very well violate the laws on user privacy and data confidentiality. Today, many parts of the world demand that technology companies treat user data carefully according to user-privacy laws. The European Union's General Data Protection Regulation (GDPR) is a prime example. In this book, we describe how federated machine learning addresses this problem with novel solutions combining distributed machine learning, cryptography and security, and incentive mechanism design based on economic principles and game theory. We explain different types of privacy-preserving machine learning solutions and their technological backgrounds, and highlight some representative practical use cases. We show how federated learning can become the foundation of next-generation machine learning that caters to technological and societal needs for responsible AI development and application.
Assistive Technology Design for Intelligence Augmentation
Assistive Technology Design for Intelligence Augmentation presents a series of frameworks, perspectives, and design guidelines drawn from disciplines spanning urban design, artificial intelligence, sociology, and new forms of collaborative work, as well as the author's experience in designing systems for people with cognitive disabilities. Many of the topics explored came from the author's graduate studies at the Center for LifeLong Learning and Design, part of the Department of Computer Science and the Institute of Cognitive Science at the University of Colorado, Boulder. The members of the Center for LifeLong Learning and Design came from a wide range of design perspectives including computer science, molecular biology, journalism, architecture, assistive technology (AT), urban design, sociology, and psychology. The main emphasis of this book is to provide leverage for understanding the problems that the AT designer faces rather than facilitating the design process itself. Looking atthe designer's task with these lenses often changes the nature of the problem to be solved. The main body of this book consists of a series of short chapters describing a particular approach, its applicability and relevance to design for intelligence augmentation in complex computationally supported systems, and examples in research and the marketplace. The final part of the book consists of listing source documents for each of the topics and a reading list for further exploration. This book provides an introduction to perspectives and frameworks that are not commonly taught in presentations of AT design which may also provide valuable design insights to general human-computer interaction and computer-supported cooperative work researchers and practitioners.
Strategic Voting
Social choice theory deals with aggregating the preferences of multiple individuals regarding several available alternatives, a situation colloquially known as voting. There are many different voting rules in use and even more in the literature, owing to the various considerations such an aggregation method should take into account. The analysis of voting scenarios becomes particularly challenging in the presence of strategic voters, that is, voters that misreport their true preferences in an attempt to obtain a more favorable outcome. In a world that is tightly connected by the Internet, where multiple groups with complex incentives make frequent joint decisions, the interest in strategic voting exceeds the scope of political science and is a focus of research in economics, game theory, sociology, mathematics, and computer science. The book has two parts. The first part asks "are there voting rules that are truthful?" in the sense that all voters have an incentive toreport their true preferences. The seminal Gibbard-Satterthwaite theorem excludes the existence of such voting rules under certain requirements. From this starting point, we survey both extensions of the theorem and various conditions under which truthful voting is made possible (such as restricted preference domains). We also explore the connections with other problems of mechanism design such as locating a facility that serves multiple users. In the second part, we ask "what would be the outcome when voters do vote strategically?" rather than trying to prevent such behavior. We overview various game-theoretic models and equilibrium concepts from the literature, demonstrate how they apply to voting games, and discuss their implications on social welfare.We conclude with a brief survey of empirical and experimental findings that could play a key role in future development of game theoretic voting models.
Network Embedding
heterogeneous graphs. Further, the book introduces different applications of NE such as recommendation and information diffusion prediction. Finally, the book concludes the methods and applications and looks forward to the future directions.
Reasoning with Probabilistic and Deterministic Graphical Models
Graphical models (e.g., Bayesian and constraint networks, influence diagrams, and Markov decision processes) have become a central paradigm for knowledge representation and reasoning in both artificial intelligence and computer science in general. These models are used to perform many reasoning tasks, such as scheduling, planning and learning, diagnosis and prediction, design, hardware and software verification, and bioinformatics. These problems can be stated as the formal tasks of constraint satisfaction and satisfiability, combinatorial optimization, and probabilistic inference. It is well known that the tasks are computationally hard, but research during the past three decades has yielded a variety of principles and techniques that significantly advanced the state of the art. This book provides comprehensive coverage of the primary exact algorithms for reasoning with such models. The main feature exploited by the algorithms is the model's graph. We present inference-based, message-passing schemes (e.g., variable-elimination) and search-based, conditioning schemes (e.g., cycle-cutset conditioning and AND/OR search). Each class possesses distinguished characteristics and in particular has different time vs. space behavior. We emphasize the dependence of both schemes on few graph parameters such as the treewidth, cycle-cutset, and (the pseudo-tree) height. The new edition includes the notion of influence diagrams, which focus on sequential decision making under uncertainty. We believe the principles outlined in the book would serve well in moving forward to approximation and anytime-based schemes. The target audience of this book is researchers and students in the artificial intelligence and machine learning area, and beyond.
Introduction to Logic Programming
Logic Programming is a style of programming in which programs take the form of sets of sentences in the language of Symbolic Logic. Over the years, there has been growing interest in Logic Programming due to applications in deductive databases, automated worksheets, Enterprise Management (business rules), Computational Law, and General Game Playing. This book introduces Logic Programming theory, current technology, and popular applications. In this volume, we take an innovative, model-theoretic approach to logic programming. We begin with the fundamental notion of datasets, i.e., sets of ground atoms. Given this fundamental notion, we introduce views, i.e., virtual relations; and we define classical logic programs as sets of view definitions, written using traditional Prolog-like notation but with semantics given in terms of datasets rather than implementation. We then introduce actions, i.e., additions and deletions of ground atoms; and we define dynamic logic programs as sets of action definitions. In addition to the printed book, there is an online version of the text with an interpreter and a compiler for the language used in the text and an integrated development environment for use in developing and deploying practical logic programs.
Computational Aspects of Cooperative Game Theory
Cooperative game theory is a branch of (micro-)economics that studies the behavior of self-interested agents in strategic settings where binding agreements among agents are possible. Our aim in this book is to present a survey of work on the computational aspects of cooperative game theory. We begin by formally defining transferable utility games in characteristic function form, and introducing key solution concepts such as the core and the Shapley value. We then discuss two major issues that arise when considering such games from a computational perspective: identifying compact representations for games, and the closely related problem of efficiently computing solution concepts for games. We survey several formalisms for cooperative games that have been proposed in the literature, including, for example, cooperative games defined on networks, as well as general compact representation schemes such as MC-nets and skill games. As a detailed case study, we consider weighted voting games: a widely-used and practically important class of cooperative games that inherently have a natural compact representation. We investigate the complexity of solution concepts for such games, and generalizations of them. We briefly discuss games with non-transferable utility and partition function games. We then overview algorithms for identifying welfare-maximizing coalition structures and methods used by rational agents to form coalitions (even under uncertainty), including bargaining algorithms. We conclude by considering some developing topics, applications, and future research directions.
Learning and Decision-Making from Rank Data
The ubiquitous challenge of learning and decision-making from rank data arises in situations where intelligent systems collect preference and behavior data from humans, learn from the data, and then use the data to help humans make efficient, effective, and timely decisions. Often, such data are represented by rankings. This book surveys some recent progress toward addressing the challenge from the considerations of statistics, computation, and socio-economics. We will cover classical statistical models for rank data, including random utility models, distance-based models, and mixture models. We will discuss and compare classical and state-of-the-art algorithms, such as algorithms based on Minorize-Majorization (MM), Expectation-Maximization (EM), Generalized Method-of-Moments (GMM), rank breaking, and tensor decomposition. We will also introduce principled Bayesian preference elicitation frameworks for collecting rank data. Finally, we will examine socio-economic aspects of statistically desirable decision-making mechanisms, such as Bayesian estimators. This book can be useful in three ways: (1) for theoreticians in statistics and machine learning to better understand the considerations and caveats of learning from rank data, compared to learning from other types of data, especially cardinal data; (2) for practitioners to apply algorithms covered by the book for sampling, learning, and aggregation; and (3) as a textbook for graduate students or advanced undergraduate students to learn about the field. This book requires that the reader has basic knowledge in probability, statistics, and algorithms. Knowledge in social choice would also help but is not required.
Transfer Learning for Multiagent Reinforcement Learning Systems
Learning to solve sequential decision-making tasks is difficult. Humans take years exploring the environment essentially in a random way until they are able to reason, solve difficult tasks, and collaborate with other humans towards a common goal. Artificial Intelligent agents are like humans in this aspect. Reinforcement Learning (RL) is a well-known technique to train autonomous agents through interactions with the environment. Unfortunately, the learning process has a high sample complexity to infer an effective actuation policy, especially when multiple agents are simultaneously actuating in the environment. However, previous knowledge can be leveraged to accelerate learning and enable solving harder tasks. In the same way humans build skills and reuse them by relating different tasks, RL agents might reuse knowledge from previously solved tasks and from the exchange of knowledge with other agents in the environment. In fact, virtually all of the most challenging tasks currently solved by RL rely on embedded knowledge reuse techniques, such as Imitation Learning, Learning from Demonstration, and Curriculum Learning. This book surveys the literature on knowledge reuse in multiagent RL. The authors define a unifying taxonomy of state-of-the-art solutions for reusing knowledge, providing a comprehensive discussion of recent progress in the area. In this book, readers will find a comprehensive discussion of the many ways in which knowledge can be reused in multiagent sequential decision-making tasks, as well as in which scenarios each of the approaches is more efficient. The authors also provide their view of the current low-hanging fruit developments of the area, as well as the still-open big questions that could result in breakthrough developments. Finally, the book provides resources to researchers who intend to join this area or leverage those techniques, including a list of conferences, journals, and implementation tools. This book will be useful for a wide audience; and will hopefully promote new dialogues across communities and novel developments in the area.
Introduction to Intelligent Systems in Traffic and Transportation
Urban mobility is not only one of the pillars of modern economic systems, but also a key issue in the quest for equality of opportunity, once it can improve access to other services. Currently, however, there are a number of negative issues related to traffic, especially in mega-cities, such as economical issues (cost of opportunity caused by delays), environmental (externalities related to emissions of pollutants), and social (traffic accidents). Solutions to these issues are more and more closely tied to information and communication technology. Indeed, a search in the technical literature (using the keyword ``urban traffic" to filter out articles on data network traffic) retrieved the following number of articles (as of December 3, 2013): 9,443 (ACM Digital Library), 26,054 (Scopus), and 1,730,000 (Google Scholar). Moreover, articles listed in the ACM query relate to conferences as diverse as MobiCom, CHI, PADS, and AAMAS. This means that there is a big and diverse community of computer scientists and computer engineers who tackle research that is connected to the development of intelligent traffic and transportation systems. It is also possible to see that this community is growing, and that research projects are getting more and more interdisciplinary. To foster the cooperation among the involved communities, this book aims at giving a broad introduction into the basic but relevant concepts related to transportation systems, targeting researchers and practitioners from computer science and information technology. In addition, the second part of the book gives a panorama of some of the most exciting and newest technologies, originating in computer science and computer engineering, that are now being employed in projects related to car-to-car communication, interconnected vehicles, car navigation, platooning, crowd sensing and sensor networks, among others. This material will also be of interest to engineers and researchers from the traffic and transportation community.
Multi-Modal Face Presentation Attack Detection
For the last ten years, face biometric research has been intensively studied by the computer vision community. Face recognition systems have been used in mobile, banking, and surveillance systems. For face recognition systems, face spoofing attack detection is a crucial stage that could cause severe security issues in government sectors. Although effective methods for face presentation attack detection have been proposed so far, the problem is still unsolved due to the difficulty in the design of features and methods that can work for new spoofing attacks. In addition, existing datasets for studying the problem are relatively small which hinders the progress in this relevant domain. In order to attract researchers to this important field and push the boundaries of the state of the art on face anti-spoofing detection, we organized the Face Spoofing Attack Workshop and Competition at CVPR 2019, an event part of the ChaLearn Looking at People Series. As part of this event, we released the largest multi-modal face anti-spoofing dataset so far, the CASIA-SURF benchmark. The workshop reunited many researchers from around the world and the challenge attracted more than 300 teams. Some of the novel methodologies proposed in the context of the challenge achieved state-of-the-art performance. In this manuscript, we provide a comprehensive review on face anti-spoofing techniques presented in this joint event and point out directions for future research on the face anti-spoofing field.
Active Learning
The key idea behind active learning is that a machine learning algorithm can perform better with less training if it is allowed to choose the data from which it learns. An active learner may pose "queries," usually in the form of unlabeled data instances to be labeled by an "oracle" (e.g., a human annotator) that already understands the nature of the problem. This sort of approach is well-motivated in many modern machine learning and data mining applications, where unlabeled data may be abundant or easy to come by, but training labels are difficult, time-consuming, or expensive to obtain. This book is a general introduction to active learning. It outlines several scenarios in which queries might be formulated, and details many query selection algorithms which have been organized into four broad categories, or "query selection frameworks." We also touch on some of the theoretical foundations of active learning, and conclude with an overview of the strengths and weaknesses of these approaches in practice, including a summary of ongoing work to address these open challenges and opportunities. Table of Contents: Automating Inquiry / Uncertainty Sampling / Searching Through the Hypothesis Space / Minimizing Expected Error and Variance / Exploiting Structure in Data / Theory / Practical Considerations
A Concise Introduction to Models and Methods for Automated Planning
Planning is the model-based approach to autonomous behavior where the agent behavior is derived automatically from a model of the actions, sensors, and goals. The main challenges in planning are computational as all models, whether featuring uncertainty and feedback or not, are intractable in the worst case when represented in compact form. In this book, we look at a variety of models used in AI planning, and at the methods that have been developed for solving them. The goal is to provide a modern and coherent view of planning that is precise, concise, and mostly self-contained, without being shallow. For this, we make no attempt at covering the whole variety of planning approaches, ideas, and applications, and focus on the essentials. The target audience of the book are students and researchers interested in autonomous behavior and planning from an AI, engineering, or cognitive science perspective. Table of Contents: Preface / Planning and Autonomous Behavior / Classical Planning: Full Information and Deterministic Actions / Classical Planning: Variations and Extensions / Beyond Classical Planning: Transformations / Planning with Sensing: Logical Models / MDP Planning: Stochastic Actions and Full Feedback / POMDP Planning: Stochastic Actions and Partial Feedback / Discussion / Bibliography / Author's Biography
Multi-Objective Decision Making
Many real-world decision problems have multiple objectives. For example, when choosing a medical treatment plan, we want to maximize the efficacy of the treatment, but also minimize the side effects. These objectives typically conflict, e.g., we can often increase the efficacy of the treatment, but at the cost of more severe side effects. In this book, we outline how to deal with multiple objectives in decision-theoretic planning and reinforcement learning algorithms. To illustrate this, we employ the popular problem classes of multi-objective Markov decision processes (MOMDPs) and multi-objective coordination graphs (MO-CoGs). First, we discuss different use cases for multi-objective decision making, and why they often necessitate explicitly multi-objective algorithms. We advocate a utility-based approach to multi-objective decision making, i.e., that what constitutes an optimal solution to a multi-objective decision problem should be derived from the availableinformation about user utility. We show how different assumptions about user utility and what types of policies are allowed lead to different solution concepts, which we outline in a taxonomy of multi-objective decision problems. Second, we show how to create new methods for multi-objective decision making using existing single-objective methods as a basis. Focusing on planning, we describe two ways to creating multi-objective algorithms: in the inner loop approach, the inner workings of a single-objective method are adapted to work with multi-objective solution concepts; in the outer loop approach, a wrapper is created around a single-objective method that solves the multi-objective problem as a series of single-objective problems. After discussing the creation of such methods for the planning setting, we discuss how these approaches apply to the learning setting. Next, we discuss three promising application domains for multi-objective decision making algorithms: energy, health, and infrastructure and transportation. Finally, we conclude by outlining important open problems and promising future directions.
Robot Learning from Human Demonstration
Learning from Demonstration (LfD) explores techniques for learning a task policy from examples provided by a human teacher. The field of LfD has grown into an extensive body of literature over the past 30 years, with a wide variety of approaches for encoding human demonstrations and modeling skills and tasks. Additionally, we have recently seen a focus on gathering data from non-expert human teachers (i.e., domain experts but not robotics experts). In this book, we provide an introduction to the field with a focus on the unique technical challenges associated with designing robots that learn from naive human teachers. We begin, in the introduction, with a unification of the various terminology seen in the literature as well as an outline of the design choices one has in designing an LfD system. Chapter 2 gives a brief survey of the psychology literature that provides insights from human social learning that are relevant to designing robotic social learners. Chapter 3 walks through an LfD interaction, surveying the design choices one makes and state of the art approaches in prior work. First, is the choice of input, how the human teacher interacts with the robot to provide demonstrations. Next, is the choice of modeling technique. Currently, there is a dichotomy in the field between approaches that model low-level motor skills and those that model high-level tasks composed of primitive actions. We devote a chapter to each of these. Chapter 7 is devoted to interactive and active learning approaches that allow the robot to refine an existing task model. And finally, Chapter 8 provides best practices for evaluation of LfD systems, with a focus on how to approach experiments with human subjects in this domain.
An Introduction to Constraint-Based Temporal Reasoning
Solving challenging computational problems involving time has been a critical component in the development of artificial intelligence systems almost since the inception of the field. This book provides a concise introduction to the core computational elements of temporal reasoning for use in AI systems for planning and scheduling, as well as systems that extract temporal information from data. It presents a survey of temporal frameworks based on constraints, both qualitative and quantitative, as well as of major temporal consistency techniques. The book also introduces the reader to more recent extensions to the core model that allow AI systems to explicitly represent temporal preferences and temporal uncertainty. This book is intended for students and researchers interested in constraint-based temporal reasoning. It provides a self-contained guide to the different representations of time, as well as examples of recent applications of time in AI systems.
Trading Agents
Automated trading in electronic markets is one of the most common and consequential applications of autonomous software agents. Design of effective trading strategies requires thorough understanding of how market mechanisms operate, and appreciation of strategic issues that commonly manifest in trading scenarios. Drawing on research in auction theory and artificial intelligence, this book presents core principles of strategic reasoning that apply to market situations. The author illustrates trading strategy choices through examples of concrete market environments, such as eBay, as well as abstract market models defined by configurations of auctions and traders. Techniques for addressing these choices constitute essential building blocks for the design of trading strategies for rich market applications. The lecture assumes no prior background in game theory or auction theory, or artificial intelligence. Table of Contents: Introduction / Example: Bidding on eBay / Auction Fundamentals /Continuous Double Auctions / Interdependent Markets / Conclusion
Graph-Based Semi-Supervised Learning
While labeled data is expensive to prepare, ever increasing amounts of unlabeled data is becoming widely available. In order to adapt to this phenomenon, several semi-supervised learning (SSL) algorithms, which learn from labeled as well as unlabeled data, have been developed. In a separate line of work, researchers have started to realize that graphs provide a natural way to represent data in a variety of domains. Graph-based SSL algorithms, which bring together these two lines of work, have been shown to outperform the state-of-the-art in many applications in speech processing, computer vision, natural language processing, and other areas of Artificial Intelligence. Recognizing this promising and emerging area of research, this synthesis lecture focuses on graph-based SSL algorithms (e.g., label propagation methods). Our hope is that after reading this book, the reader will walk away with the following: (1) an in-depth knowledge of the current state-of-the-art in graph-based SSL algorithms, and the ability to implement them; (2) the ability to decide on the suitability of graph-based SSL methods for a problem; and (3) familiarity with different applications where graph-based SSL methods have been successfully applied. Table of Contents: Introduction / Graph Construction / Learning and Inference / Scalability / Applications / Future Work / Bibliography / Authors' Biographies / Index
Representations and Techniques for 3D Object Recognition and Scene Interpretation
One of the grand challenges of artificial intelligence is to enable computers to interpret 3D scenes and objects from imagery. This book organizes and introduces major concepts in 3D scene and object representation and inference from still images, with a focus on recent efforts to fuse models of geometry and perspective with statistical machine learning. The book is organized into three sections: (1) Interpretation of Physical Space; (2) Recognition of 3D Objects; and (3) Integrated 3D Scene Interpretation. The first discusses representations of spatial layout and techniques to interpret physical scenes from images. The second section introduces representations for 3D object categories that account for the intrinsically 3D nature of objects and provide robustness to change in viewpoints. The third section discusses strategies to unite inference of scene geometry and object pose and identity into a coherent scene interpretation. Each section broadly surveys important ideas from cognitive science and artificial intelligence research, organizes and discusses key concepts and techniques from recent work in computer vision, and describes a few sample approaches in detail. Newcomers to computer vision will benefit from introductions to basic concepts, such as single-view geometry and image classification, while experts and novices alike may find inspiration from the book's organization and discussion of the most recent ideas in 3D scene understanding and 3D object recognition. Specific topics include: mathematics of perspective geometry; visual elements of the physical scene, structural 3D scene representations; techniques and features for image and region categorization; historical perspective, computational models, and datasets and machine learning techniques for 3D object recognition; inferences of geometrical attributes of objects, such as size and pose; and probabilistic and feature-passing approaches for contextual reasoning about 3D objects and scenes. Table of Contents: Background on 3D Scene Models / Single-view Geometry / Modeling the Physical Scene / Categorizing Images and Regions / Examples of 3D Scene Interpretation / Background on 3D Recognition / Modeling 3D Objects / Recognizing and Understanding 3D Objects / Examples of 2D 1/2 Layout Models / Reasoning about Objects and Scenes / Cascades of Classifiers / Conclusion and Future Directions
Essential Principles for Autonomous Robotics
From driving, flying, and swimming, to digging for unknown objects in space exploration, autonomous robots take on varied shapes and sizes. In part, autonomous robots are designed to perform tasks that are too dirty, dull, or dangerous for humans. With nontrivial autonomy and volition, they may soon claim their own place in human society. These robots will be our allies as we strive for understanding our natural and man-made environments and build positive synergies around us. Although we may never perfect replication of biological capabilities in robots, we must harness the inevitable emergence of robots that synchronizes with our own capacities to live, learn, and grow. This book is a snapshot of motivations and methodologies for our collective attempts to transform our lives and enable us to cohabit with robots that work with and for us. It reviews and guides the reader to seminal and continual developments that are the foundations for successful paradigms. It attempts to demystifythe abilities and limitations of robots. It is a progress report on the continuing work that will fuel future endeavors. Table of Contents: Part I: Preliminaries/Agency, Motion, and Anatomy/Behaviors / Architectures / Affect/Sensors / Manipulators/Part II: Mobility/Potential Fields/Roadmaps / Reactive Navigation / Multi-Robot Mapping: Brick and Mortar Strategy / Part III: State of the Art / Multi-Robotics Phenomena / Human-Robot Interaction / Fuzzy Control / Decision Theory and Game Theory / Part IV: On the Horizon / Applications: Macro and Micro Robots / References / Author Biography / Discussion
Predicting Human Decision-Making
Human decision-making often transcends our formal models of "rationality." Designing intelligent agents that interact proficiently with people necessitates the modeling of human behavior and the prediction of their decisions. In this book, we explore the task of automatically predicting human decision-making and its use in designing intelligent human-aware automated computer systems of varying natures--from purely conflicting interaction settings (e.g., security and games) to fully cooperative interaction settings (e.g., autonomous driving and personal robotic assistants). We explore the techniques, algorithms, and empirical methodologies for meeting the challenges that arise from the above tasks and illustrate major benefits from the use of these computational solutions in real-world application domains such as security, negotiations, argumentative interactions, voting systems, autonomous driving, and games. The book presents both the traditional and classical methods as well asthe most recent and cutting edge advances, providing the reader with a panorama of the challenges and solutions in predicting human decision-making.
Cybersecurity, Privacy and Freedom Protection in the Connected World
This book provides an opportunity for investigators, government officials, systems scientists, strategists, assurance researchers, owners, operators and maintainers of large, complex and advanced systems and infrastructures to update their knowledge with the state of best practice in the challenging domains whilst networking with the leading representatives, researchers and solution providers. Drawing on 12 years of successful events on information security, digital forensics and cyber-crime, the 13th ICGS3-20 conference aims to provide attendees with an information-packed agenda with representatives from across the industry and the globe. The challenges of complexity, rapid pace of change and risk/opportunity issues associated with modern products, systems, special events and infrastructures. In an era of unprecedented volatile, political and economic environment across the world, computer-based systems face ever more increasing challenges, disputes and responsibilities, and whilst the Internet has created a global platform for the exchange of ideas, goods and services, it has also created boundless opportunities for cyber-crime. As an increasing number of large organizations and individuals use the Internet and its satellite mobile technologies, they are increasingly vulnerable to cyber-crime threats. It is therefore paramount that the security industry raises its game to combat these threats. Whilst there is a huge adoption of technology and smart home devices, comparably, there is a rise of threat vector in the abuse of the technology in domestic violence inflicted through IoT too. All these are an issue of global importance as law enforcement agencies all over the world are struggling to cope.
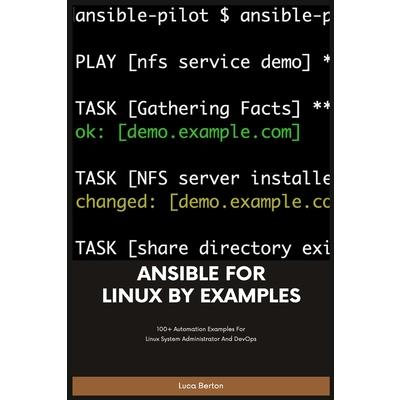
Ansible For Linux by Examples
Ansible is an Open Source IT automation tool. This book contains all of the obvious and not-so-obvious best practices of Ansible automation. Every successful IT department needs automation nowadays for bare metal servers, virtual machines, could, containers, and edge computing. Automate your IT journey with Ansible automation technology. You are going to start with the installation of Ansible in Enterprise and Community Linux using the most command package manager and archives.Each of the 100+ lessons summarizes a module: from the most important parameter to some Ansible code and real-life usage. Each code is battle proved in the real life. Simplifying mundane activities like creating a text file, extracting and archiving, and fetching a repository using HTTPS or SSH connections could be automated with some lines of code and these are only some of the long lists included in the course.There are some Ansible codes usable in all the Linux systems, some specific for RedHat-like, Debian-like, and Suse-like.The 20+ Ansible troubleshooting lesson teaches you how to read the error message, how to reproduce it, and the process of troubleshooting and resolution.Are you ready to automate your day with Ansible?Examples in the book are tested with the latest version of Ansible 2.9+ and Ansible Core 2.11+.
Artificial Intelligence and the Fourth Industrial Revolution
This book presents the overall technology spectrum in artificial intelligence (AI) and the Fourth Industrial Revolution, which is set to revolutionize the world. It discusses their various aspects and related case studies from industry, academics, administration, law, finance, and accounting as well as educational technology. The contributors, who are experts in their respective fields and from industry and academia, focus on a gesture-recognition prototype for specially abled people; jurisprudential approach to AI and legal reasoning; automated chatbot for autism spectrum disorder using AI assistance; Big Data analytics and Internet of Things (IoT); role of AI in advancement of drug discovery; development, opportunities, and challenges of the Fourth Industrial Revolution; legal, ethical, and policy implications of AI; Internet of Health Things for smart healthcare and digital wellbeing; machine learning and computer vision; computer vision-based system for automation and industrial applications; AI-IoT in home-based healthcare; and AI in super-precision human brain and spine surgery. Buttressed with comprehensive theoretical, methodological, well-established, and validated empirical examples, the book covers the interests of a broad audience from basic science to engineering and technology experts and learners. It will be greatly helpful for CEOs, entrepreneurs, academic leaders, researchers, and students of engineering, biomedicine, and master's programs in science as well as the vast workforce and students with technical or non-technical backgrounds. It also serves common public interest by presenting new methods to improve the quality of life in general, with a better integration into society.
Logic Programming
Includes tutorials, lectures, and refereed papers on all aspects of logic programming, including theoretical foundations, constraints, concurrency and parallelism, deductive databases, language design and implementation, nonmonotonic reasoning, and logic programming and the Internet.The International Conference on Logic Programming, sponsored by the Association for Logic Programming, includes tutorials, lectures, and refereed papers on all aspects of logic programming, including theoretical foundations, constraints, concurrency and parallelism, deductive databases, language design and implementation, nonmonotonic reasoning, and logic programming and the Internet.
Privacy Technologies and Policy
This book constitutes the refereed conference proceedings of the 10th Annual Privacy Forum, APF 2022 in Warsaw, Poland in June 2022. The 8 full papers were carefully reviewed and selected from 38 submissions. The papers are organized in the area of privacy and data protection while focusing on privacy related application areas. A large focus of the 2022 conference was on the General Data Protection Regulation (GDPR).
The Art of Unit Testing, Third Edition
Unit testing is more than just a collection of tools and practices--it's a state of mind! This bestseller reveals the master's secrets for delivering robust, maintainable, and trustworthy code. Thousands of developers have learned to hone their code quality under the tutelage of The Art of Unit Testing. This revised third edition updates an international bestseller to reflect modern development tools and practices, as well as to cover JavaScript. Inside The Art of Unit Testing, Third Edition you will learn how to: Create readable, maintainable, and trustworthy tests Work with fakes, stubs, mock objects, and isolation frameworks Apply simple dependency injection techniques Refactor legacy code with confidence Test both frontend and backend code Effective unit tests streamline your software development process and ensure you deliver consistent high-quality code every time. With practical examples in JavaScript and Node, this hands-on guide takes you from your very first unit tests all the way to comprehensive test suites, naming standards, and refactoring techniques. You'll explore test patterns and organization, working with legacy code and even "untestable" code. The many tool-agnostic examples are presented in JavaScript and carefully designed so that they apply to code written in any language. Purchase of the print book includes a free eBook in PDF, Kindle, and ePub formats from Manning Publications. About the technology The art of unit testing is more than just learning the right collection of tools and practices. It's about understanding what makes great tests tick, finding the right strategy for each unique situation, and knowing what to do when the testing process gets messy. This book delivers insights and advice that will transform the way you test your software. About the book The Art of Unit Testing, Third Edition shows you how to create readable and maintainable tests. It goes well beyond basic test creation into organization-wide test strategies, troubleshooting, working with legacy code, and "merciless" refactoring. You'll love the practical examples and familiar scenarios that make testing come alive as you read. This third edition has been updated with techniques specific to object-oriented, functional, and modular coding styles. The examples use JavaScript. What's inside Deciding on test types and strategies Test Entry & Exit Points Refactoring legacy code Fakes, stubs, mock objects, and isolation frameworks Object-Oriented, Functional, and Modular testing styles About the reader Examples use JavaScript, TypeScript, and Node.js. About the author Roy Osherove is an internationally-recognized expert in unit testing and agile software methodology. Vladimir Khorikov is the author of Manning's Unit Testing Principles, Practices, and Patterns, a Pluralsight author, and a Microsoft MVP. Table of Contents PART 1 1 The basics of unit testing 2 A first unit test PART 2 3 Breaking dependencies with stubs 4 Interaction testing using mock objects 5 Isolation frameworks 6 Unit testing asynchronous code PART 3 7 Trustworthy tests 8 Maintainability PART 4 9 Readability 10 Developing a testing strategy 11 Integrating unit testing into the organization 12 Working with legacy code Appendix Monkey-patching functions and modules
Silicon Second Nature
Silicon Second Nature takes us on an expedition into an extraordinary world where nature is made of bits and bytes and life is born from sequences of zeroes and ones. Artificial Life is the brainchild of scientists who view self-replicating computer programs--such as computer viruses--as new forms of life. Anthropologist Stefan Helmreich's look at the social and simulated worlds of Artificial Life--primarily at the Santa Fe Institute, a well-known center for studies in the sciences of complexity--introduces readers to the people and programs connected with this unusual hybrid of computer science and biology.When biology becomes an information science, when DNA is downloaded into virtual reality, new ways of imagining "life" become possible. Through detailed dissections of the artifacts of Artifical Life, Helmreich explores how these novel visions of life are recombining with the most traditional tales told by Western culture. Because Artificial Life scientists tend to see themselves as masculine gods of their cyberspace creations, as digital Darwins exploring frontiers filled with primitive creatures, their programs reflect prevalent representations of gender, kinship, and race, and repeat origin stories most familiar from mythical and religious narratives.But Artificial Life does not, Helmreich says, simply reproduce old stories in new software. Much like contemporary activities of cloning, cryonics, and transgenics, the practice of simulating and synthesizing life in silico challenges and multiplies the very definition of vitality. Are these models, as some would claim, actually another form of the real thing? Silicon Second Nature takes Artifical Life as a symptom and source of our mutating visions of life itself.
The Cult of Information
As we devote ever-increasing resources to providing, or prohibiting, access to information via computer, Theodore Roszak reminds us that voluminous information does not necessarily lead to sound thinking. "Data glut" obscures basic questions of justice and purpose and may even hinder rather than enhance our productivity. In this revised and updated edition of The Cult of Information, Roszak reviews the disruptive role the computer has come to play in international finance and the way in which "edutainment" software and computer games degrade the literacy of children. At the same time, he finds hopeful new ways in which the library and free citizens' access to the Internet and the national data-highway can turn computer technology into a democratic and liberating force. Roszak's examination of the place of computer technology in our culture is essential reading for all those who use computers, who are intimidated by computers, or who are concerned with the appropriate role of computers in the education of our children.
Machine Learning
This book introduces machine learning for readers with some background in basic linear algebra, statistics, probability, and programming. In a coherent statistical framework it covers a selection of supervised machine learning methods, from the most fundamental (k-NN, decision trees, linear and logistic regression) to more advanced methods (deep neural networks, support vector machines, Gaussian processes, random forests and boosting), plus commonly-used unsupervised methods (generative modeling, k-means, PCA, autoencoders and generative adversarial networks). Careful explanations and pseudo-code are presented for all methods. The authors maintain a focus on the fundamentals by drawing connections between methods and discussing general concepts such as loss functions, maximum likelihood, the bias-variance decomposition, ensemble averaging, kernels and the Bayesian approach along with generally useful tools such as regularization, cross validation, evaluation metrics and optimization methods. The final chapters offer practical advice for solving real-world supervised machine learning problems and on ethical aspects of modern machine learning.
Combining Dataops, Mlops and Devops
Accelerate the delivery of software, data, and machine learning KEY FEATURES ● Each chapter harmonizes the DevOps, Data Engineering, and Optimized Machine Learning cultures.● Equips readers with AGILE skills to continuously re-prioritize production backlogs.● Containerization, Docker, Kubernetes, DataOps, and MLOps are all rolled together. DESCRIPTION This book instructs readers on how to operationalize the creation of systems, software applications, and business information using the best practices of DevOps, DataOps, and MLOps, among other things.From software unit packaging code and its dependencies to automating the software development lifecycle and deployment, the book provides a learning roadmap that begins with the basics and progresses to advanced topics. This book teaches you how to create a culture of cooperation, affinity, and tooling at scale using DevOps, Docker, Kubernetes, Data Engineering, and Machine Learning. Microservices design, setting up clusters and maintaining them, processing data pipelines, and automating operations with machine learning are all topics that will aid you in your career. When you use each of the xOps methods described in the book, you will notice a clear shift in your understanding of system development.Throughout the book, you will see how every stage of software development is modernized with the most up-to-date technologies and the most effective project management approaches.WHAT YOU WILL LEARN● Learn about the Packaging code and all its dependencies in a container.● Utilize DevOps to automate every stage of software development.● Learn how to create Microservices that are focused on a specific issue.● Utilize Kubernetes to containerize applications in a variety of settings.● Using DataOps, you can align people, processes, and technology.WHO THIS BOOK IS FORThis book is meant for the Software Engineering team, Data Professionals, IT Operations and Application Development Team with prior knowledge in software development.
Sonic Interactions in Virtual Environments
This open access book tackles the design of 3D spatial interactions in an audio-centered and audio-first perspective, providing the fundamental notions related to the creation and evaluation of immersive sonic experiences. The key elements that enhance the sensation of place in a virtual environment (VE) are: Immersive audio: the computational aspects of the acoustical-space properties of Virutal Reality (VR) technologies Sonic interaction: the human-computer interplay through auditory feedback in VEVR systems: naturally support multimodal integration, impacting different application domainsSonic Interactions in Virtual Environments will feature state-of-the-art research on real-time auralization, sonic interaction design in VR, quality of the experience in multimodal scenarios, and applications. Contributors and editors include interdisciplinary experts from the fields of computer science, engineering, acoustics, psychology, design, humanities, and beyond. Their mission is to shape an emerging new field of study at the intersection of sonic interaction design and immersive media, embracing an archipelago of existing research spread in different audio communities and to increase among the VR communities, researchers, and practitioners, the awareness of the importance of sonic elements when designing immersive environments.
Future-Proofing
Innovative research solutions increasingly require deep engagement with practitioners to manage the complex problems they are attempting to solve. This often project-based research is equipped with finite resources over a limited period without much thought into future-proofing the practice. These projects must face questions of what happens when a product comes to an end and whether there are any lasting positive effects once the IT systems are no longer being actively developed. From a computing perspective, the challenge is to design IT artifacts that contribute to improving the user's work and everyday life in a sustainable way, thereby also contributing to social and ecological sustainability. Future-Proofing: Making Practice-Based IT Design Sustainable documents the experiences made by several leading research groups in Europe, North America, and South Africa. It describes their efforts to achieve sustainable design results, the difficulties that barred the way but also the strategies they adopted to achieve the goal of sustainability. The analysis of these cases has inspired thinking about how to more systematically address and possibly overcome the impediments to sustainability. This book develops a strong future-oriented perspective that conceptualizes sustainability as a complex and highly variegated issue and formulates insights and recommendations with a view to help researchers to better design for sustainability.
Product Management in Practice
Product management has become a critical function for modern organizations, from small startups to corporate enterprises. And yet, the day-to-day work of product management remains largely misunderstood. In theory, product managers are high-flying visionaries who build products that people love. In practice, they're hard-working facilitators who bring clarity and focus to their teams. In this thoroughly revised and expanded edition, Matt LeMay provides real-world guidance for current and aspiring product managers. Updated for the era of remote and hybrid work, this book provides actionable answers to product management's most persistent and confounding questions, starting with: What exactly am I supposed to do all day? With this book, you'll learn: What the day-to-day work of product management entails--and how to excel at it Why no job title or description will resolve the ambiguity of your role How to bridge the false dichotomy between "strategy" and "execution" Why the temptation to focus on decks and documentation can be bad for your team (and for you) How to prioritize your time and pick your battles
MS-700 Managing Microsoft Teams Exam Guide - Second Edition
A detailed guide to preparing for the MS-700 exam and earning associate-level Microsoft Teams administrator certificationKey Features: - Plan and design your Microsoft Teams deployment- Prepare, implement, and manage policies for Microsoft Teams and for apps within Teams- Work with self-assessment questions and a mock exam and take the MS-700 certification exam with confidenceBook Description: Exam MS-700: Managing Microsoft Teams tests your knowledge and competence in the deployment, management, and monitoring of Microsoft Teams features within the Microsoft 365 platform.This book will teach you how to effectively plan and implement the required services using both the Teams admin centre within Microsoft 365 and Windows PowerShell. Throughout the chapters, you'll learn about all the policies relating to messaging, teams, meetings, and more; get to grips with the settings; and explore configuration options that a Teams administrator would encounter in their day-to-day responsibilities. You'll also discover best practices for rolling out and managing Teams services for users within your Microsoft 365 tenant as you explore each objective in detail.By the end of this Microsoft Teams book, you'll have covered everything you need to pass the MS-700 certification exam and have a handy, on-the-job desktop reference guide.What You Will Learn: - Plan and configure network settings and licensing for Microsoft Teams- Plan and configure security, compliance, and governance for Microsoft Teams- Manage users and configure guest and external access- Configure and manage Microsoft Teams devices- Create and manage teams, channels, and core experiences- Manage Phone System and numbers for Microsoft Teams- Troubleshoot audio, video, client, and environment issues- Practice with a mock exam with answers and explanationsWho this book is for: This book is for IT professionals who want to earn the Microsoft 365 Certified: Teams Administrator Associate certification. Familiarity with the principles of administering core features and services within a Microsoft 365 tenant and a basic understanding of Microsoft Teams features are needed. Prior knowledge of other Microsoft 365 workloads such as Security & Compliance will also be beneficial. To maximize the odds of passing the MS-700 exam, use this exam guide's content and practice questions to prepare alongside practicing concepts first-hand when possible.Table of Contents- Planning and configuring network settings for Microsoft Teams- Identifying Licensing Requirements for Microsoft Teams- Planning and Configuring Security and Compliance Settings for Microsoft Teams- Planning and Implementing Governance and Life Cycle Management for Microsoft Teams- Configuring and Managing External and Guest Users- Configuring and Managing Microsoft Teams Devices- Creating and managing teams- Planning and Managing Channels- Managing Chat and Collaboration Experiences- Managing Apps for Microsoft Teams- Managing Meeting Experiences- Managing Phone Numbers- Managing Phone System for Microsoft Teams- Monitoring and Reporting on a Microsoft Teams Environment- Troubleshooting Audio, Video, and Client Issues- Mock Exam- Mock Exam Answers- Assessments
Persuasive Technology
This book constitutes the refereed post-conference proceedings of the 17th International Conference on Persuasive Technology, PERSUASIVE 2022, held as a virtual event, in March 2022. The 13 full papers presented in this book together with 7 short papers were carefully reviewed and selected from 46 submissions.
Kernel Methods for Machine Learning with Math and Python
The most crucial ability for machine learning and data science is mathematical logic for grasping their essence rather than relying on knowledge or experience. This textbook addresses the fundamentals of kernel methods for machine learning by considering relevant math problems and building Python programs. The book's main features are as follows: The content is written in an easy-to-follow and self-contained style.The book includes 100 exercises, which have been carefully selected and refined. As their solutions are provided in the main text, readers can solve all of the exercises by reading the book.The mathematical premises of kernels are proven and the correct conclusions are provided, helping readers to understand the nature of kernels.Source programs and running examples are presented to help readers acquire a deeper understanding of the mathematics used.Once readers have a basic understanding of the functional analysistopics covered in Chapter 2, the applications are discussed in the subsequent chapters. Here, no prior knowledge of mathematics is assumed.This book considers both the kernel for reproducing kernel Hilbert space (RKHS) and the kernel for the Gaussian process; a clear distinction is made between the two.
Infrastructure Automation with Terraform
Use Terraform and Jenkins to implement Infrastructure as Code and Pipeline as Code across multi-cloud environmentsKey FeaturesStep-by-step guidelines for managing infrastructure across multiple cloud platforms.Expert-led coverage on managing Pipeline as Code using Jenkins.Includes images demonstrating how to manage AWS and Azure resources using Terraform Modules.DescriptionThis book explains how to quickly learn and utilize Terraform to incorporate Infrastructure as Code into a continuous integration and continuous delivery pipeline. The book gives you the step-by-step instructions with screenshots and diagrams to make the learning more accessible and fun.This book discusses the necessity of Infrastructure as a Code (IaC) and the many tools available for implementing IaC. You will gain the knowledge of resource creation, IAM roles, EC2 instances, elastic load balancers, and building terraform scripts, among other learnings. Next, you will explore projects and use-cases for implementing DevOps concepts like Continuous Integration, Infrastructure as Code, and Continuous Delivery. Finally, you learn about the Terraform Modules and how to establish networks and Kubernetes clusters on various cloud providers. Installing and configuring Jenkins and SonarQube in Cloud Environments will also be discussed.As a result of reading this book, you will be able to apply Infrastructure as Code and Pipeline as Code principles to major cloud providers such as AWS and Azure.What you will learnCreate, manage, and maintain AWS and Microsoft Azure infrastructure.Using Packer, create AMIs and EC2 instances.Utilize Terraform Modules to create VPC and Kubernetes clusters.Put the Pipeline and Infrastructure as Code principles into practice.Utilize Jenkins to automate the application lifecycle management process.Who this book is forThis book will primarily help DevOps, Cloud Operations, Agile teams, Cloud Native Developers, and Networking Professionals. Being familiar with the fundamentals of Cloud Computing and DevOps will be beneficial.Table of Contents1. Setting up Terraform2. Terraform Basics and Configuration3. Terraform Provisioners4. Automating Infrastructure Deployments in the AWS Using Terraform5. Automating Infrastructure Deployments in Azure Using Terraform6. Terraform Modules7. Terraform Cloud8. Terraform and Jenkins Integration9. End-to-End Application Management using TerraformRead more